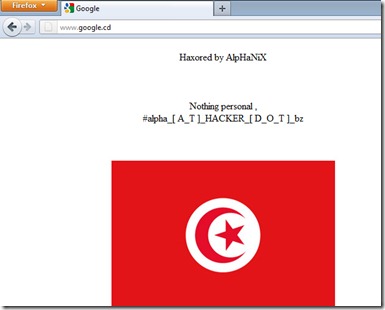
The cyber crimes of multiple kinds in Pakistan have increased by five times over the past four years. Pakistan Daily Times News today reported that, Citizen Police Liaison Committee (CPLC) Chief through a letter on Saturday, apprised the Federal Law, Justice & Parliamentary Affairs Minister that in the absence of Prevention of Electronic Crime Ordinance (PECO) Law 2007, lapsed in 2010, Pakistan had become a safe heaven for cyber criminals and con artists whereas the law enforcement agencies were unable to take legal action against them.
The cyber crimes of multiple kinds in Pakistan have increased by five times over the past four years. Pakistan Daily Times News today reported that, Citizen Police Liaison Committee (CPLC) Chief through a letter on Saturday, apprised the Federal Law, Justice & Parliamentary Affairs Minister that in the absence of Prevention of Electronic Crime Ordinance (PECO) Law 2007, lapsed in 2010, Pakistan had become a safe heaven for cyber criminals and con artists whereas the law enforcement agencies were unable to take legal action against them.
According to the Cyber Crime Unit (CCU), a branch of Pakistan's Federal Investigation Agency (FIA), 62 cases were reported to the unit in 2007, 287 cases in 2008 and the ratio dropped in 2009 but in 2010 more than 312 cases were registered in different categories of cyber crimes.
“There are numerous complaints regarding fake calls deceiving citizens into receiving a phony prize. The normal practice is that the criminals calls the supposed prize winner, and gives him three options to collect his prize money i.e. have the amount transferred in his account through cheque, visit Islamabad to receive the prize money or receive the prize at door step. Thereafter, the caller asks the victim to pay Rs 10,000 through easy paisa transfer and or by cellular easy load for the prize to be processed and once sent the receiver disappears. “ CPLC Chief said.
Cybercrime in Pakistan has its global impact especially with cyber terrorism, example of this, the disappearance of the The Wall Street Journal correspondent on Jan. 23, 2002, from Pakistan's southern city of Karachi and his captors started sending e-mails to newspapers, then the investigators starting to trace the e-mails sent by the kidnappers, this was one of the important reason for establishing the National Response Center for Cyber Crimes in Pakistan to combat against cybercrimes.
After receiving several complains, Sindh CPLC Chief Ahmed Chinoy asked FIA to take up such cases for necessary action as per law. In response to Chinoy’s letter, FIA told him that due to the absence of PECO, they were unable to take any action against the offenders.Sindh CPLC Chief wrote a letter to the Federal Law, Justice & Parliamentary Affairs Minister to draw his attention towards the PECO Law 2007, which had been lapsed in 2010.
Urging the federal minister to revoke PECO, Chinoy stated that these criminals were intentionally harming the physical, mental and financial position of their victims by using modern telecommunication networks such as internet and mobile phones.
There are a number of cyber crimes in Pakistan mainly including cyber pornography, sale of illegal articles, online gambling, intellectual property crimes, email spoofing, cyber stalking, forgery, unauthorized access to computer systems/networks, theft of information contained in electronic form, virus attacks, Trojan attacks, Internet time theft, password cracking and financial cyber crimes (hacking of ATM card numbers and bank accounts).Official data suggest that the hacking of ATM card numbers and bank accounts are on the rise in Pakistan.





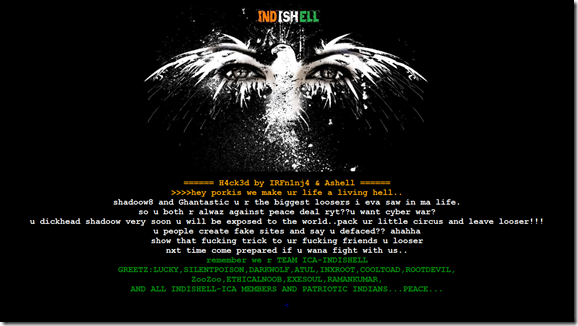

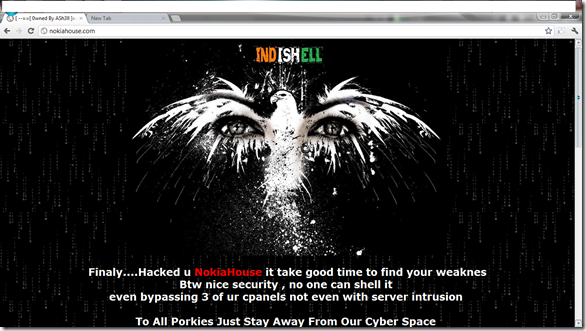


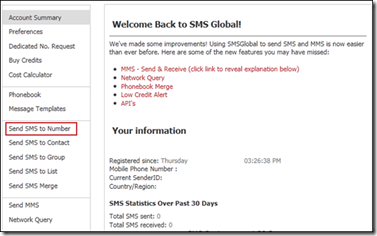
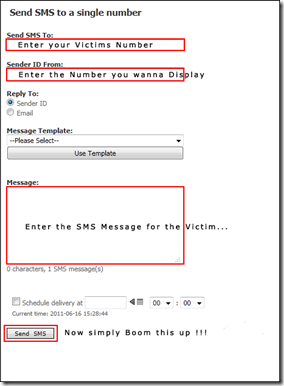 So, Enjoy Sending fake SMS to any of the number , and now you can update any buddy’s facebook status using this technique!!
So, Enjoy Sending fake SMS to any of the number , and now you can update any buddy’s facebook status using this technique!!